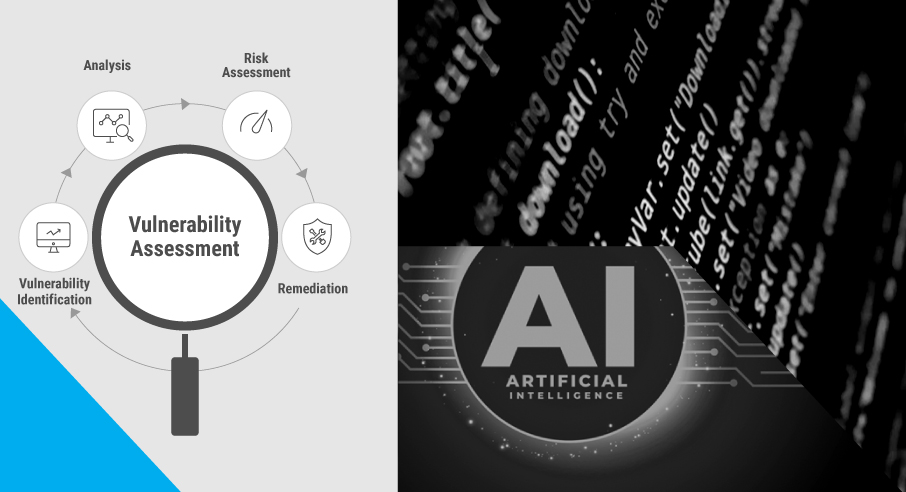
Protect High Value Assets using tailored cybersecurity solutions through ISSOaaS to safeguard agency infrastructure, networks, systems, applications, and data.
High Value Assets
Breach Detection
Adopt a multi-faceted approach to breach detection for continuous monitoring and protection of systems. Utilizing cutting-edge technologies to enhance detection capabilities and keep systems secure
Governance, Risk & Compliance
Create a cohesive strategy for managing operations, reduce risk exposure, and ensure adherence to regulatory requirements ensuring that agencies operate effectively and securely.